Phishing is still the most common entry point for cyberattacks, but most organizations are fighting it with the wrong tools.
Security awareness training teaches employees what phishing looks like.
Phishing simulations test what actually happens when it arrives.
That distinction matters more than ever.
In this guide, you’ll learn:
- What a phishing simulation actually is
- How phishing simulations work in practice
- Why security awareness training alone fails
- What separates realistic simulations from ineffective ones
- How organizations use simulations to reduce real human risk
Read More: Phishing Simulation Statistics Every Security Leader Should Know in 2026
What Is a Phishing Simulation?
A phishing simulation is a controlled cybersecurity test that mimics real-world phishing attacks to evaluate how employees behave under realistic conditions.
Instead of teaching theory, phishing simulations measure:
- How employees respond to suspicious emails
- Whether they click links or submit credentials
- How quickly they report threats
- Which roles or workflows create the highest risk
The goal is risk discovery, not employee punishment.
Phishing Simulation as a Service: Pricing, Results, and ROI
How Phishing Simulations Work (Step by Step)
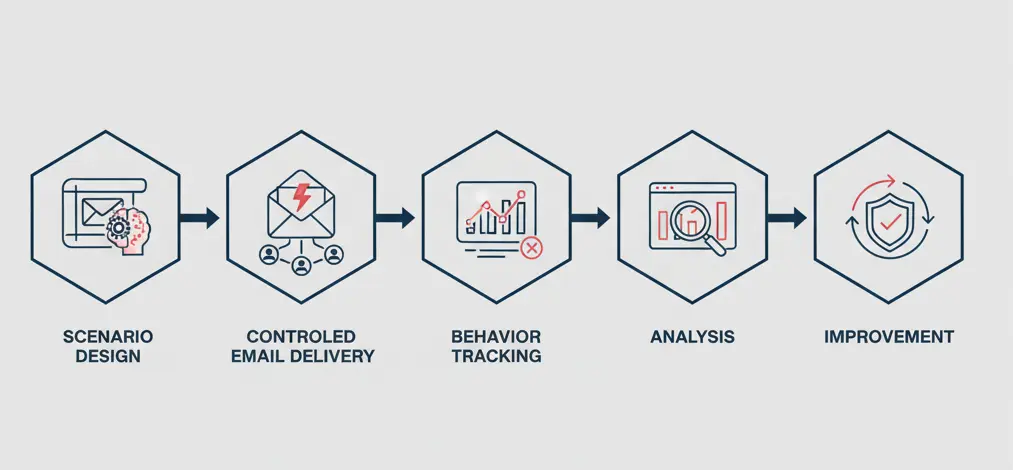
A well-designed phishing simulation follows a structured lifecycle:
1. Scenario Design
Security teams or external providers design phishing scenarios based on:
- Common attacker techniques
- Industry-relevant lures
- Typical business workflows
2. Controlled Delivery
Emails are sent in a safe, non-malicious way that poses zero operational risk.
3. Behavioural Tracking
Organizations measure:
- Opens
- Clicks
- Credential submissions
- Reporting behavior
Advanced simulations also assess potential downstream impact, not just clicks.
4. Analysis & Improvement
Results are analyzed to:
- Identify high-risk roles or patterns
- Improve reporting processes
- Refine future simulations
Phishing Simulation vs Security Awareness Training
Security awareness training and phishing simulations are often confused, but they serve very different purposes.
| Security Awareness Training | Phishing Simulation |
|---|---|
| Teaches recognition | Tests behavior |
| Knowledge-based | Risk-based |
| Passive | Active |
| Periodic | Continuous |
| Predictable | Unpredictable |
Training explains what to do.
Simulations reveal what people actually do.
Why Security Awareness Training Alone Fails
Most organizations already run phishing training—yet phishing incidents continue to rise. Why?
1. Knowledge Doesn’t Equal Behaviour
People may recognize phishing examples in training but still click under pressure, urgency, or distraction.
2. Attackers Don’t Follow Training Slides
Real attackers:
- Impersonate trusted vendors
- Exploit timing (end of quarter, payroll, audits)
- Target specific roles
Training rarely reflects this realism.
3. Familiarity Creates False Confidence
Employees often learn to recognize training patterns, not threats.
This leads to:
- Overconfidence
- Slower reporting
- Missed sophisticated attacks
What Makes a Phishing Simulation Effective?
Not all phishing simulations are equal. Many fail because they are too predictable.
An effective phishing simulation includes:
Realistic Attack Techniques
- Credential harvesting
- Business Email Compromise (BEC)
- Impersonation and pretexting
Context-Aware Targeting
- Role-specific messaging
- Workflow-based lures
- Industry language
Unpredictability
Employees shouldn’t be able to guess when or how a simulation will occur.
Risk-Focused Metrics
Beyond click rates, strong programs evaluate:
- Reporting speed
- High-risk workflows
- Behavioural trends over time
Why Realistic Phishing Simulations Matter
Phishing is not a training problem, it’s a human risk problem.
Realistic simulations help organizations:
- Identify where attackers would actually succeed
- Reduce time-to-report
- Improve incident readiness
- Provide defensible metrics to leadership and auditors
This is why many organizations turn to red team-led phishing simulations, such as those conducted by Bluefire Redteam, which are designed around real attacker behaviour rather than templates.
Are Phishing Simulations Required for Compliance?
Phishing simulations are not always explicitly mandated, but they are strongly implied or expected across major frameworks, including:
- SOC 2
- ISO 27001
- NIST Cybersecurity Framework
- HIPAA Security Rule
- GDPR security expectations
Auditors increasingly expect organizations to show evidence of active human risk testing, not just training completion.
Read More: Best Phishing Simulation Vendors (Buyer’s Guide 2026)
How Often Should Organizations Run Phishing Simulations?
Most organizations should run phishing simulations at least quarterly.
Higher-risk environments often benefit from monthly or continuous simulations.
Frequency should increase if:
- Employees handle sensitive data
- The organization has experienced phishing incidents
- There is high employee turnover
- The business operates in a regulated environment
Consistency matters more than volume.
Measuring the Real Value of Phishing Simulations
The value of phishing simulations isn’t found in perfect scores, it’s found in trend improvement.
High-value indicators include:
- Faster reporting times
- Reduced the success of sophisticated attacks
- Improved employee judgment
- A clearer understanding of organizational risk
A single prevented incident can justify years of simulation investment.
Final Takeaway: Training Educates. Simulations Reduce Risk.
Security awareness training is necessary—but insufficient on its own.
Phishing simulations:
- Expose real weaknesses
- Test real behaviour
- Reduce real risk
Organizations that rely on training alone remain vulnerable to the very attacks they think they’re prepared for.