Cyber, Social, and Physical Adversary Simulation for the Financial Sector — Powered by Bluefire Redteam
German banks are under continuous attack from cybercriminals, insider threats, state-aligned actors, and sophisticated financial fraud groups. These attackers use a combination of digital, social, and physical intrusion techniques to bypass defenses and gain access to sensitive systems.
Traditional penetration testing does not reflect this reality.
Modern financial institutions require full-spectrum Red Teaming, where adversaries simulate:
- Cyber intrusions
- Cloud identity compromise
- Lateral movement
- Social engineering
- Physical infiltration
- Insider threat behavior
This all-encompassing strategy demonstrates the bank’s actual capacity to identify, stop, and react to contemporary attacks.
In 2025, banks across Germany increasingly turn to Bluefire Redteam — the #1 provider of realistic, multi-vector adversary simulation aligned with BaFin, TIBER-EU, ECB, and NIS2 requirements.
Why Red Teaming Is Essential for Banks in Germany
Financial institutions remain one of the most heavily targeted sectors in Europe due to:
- High-value asset access
- Large, hybrid, and legacy environments
- Payment system complexity
- Human-layer vulnerability
- Massive physical attack surface
- Cloud-first identity models
- Regulatory expectations for resilience
Attackers don’t limit themselves to email phishing or endpoint exploits. They blend techniques:
- Sending phishing campaigns
- Dropping payloads at branch offices
- Social engineering staff
- Tailgating into secure floors
- Planting rogue devices
- Abusing cloud identity permissions
- Targeting SWIFT or internal payment systems
A realistic Red Team must emulate every one of these behaviors.
A Full-Spectrum Red Team Operation for Banks (The Flow)
Engagements are organized by Bluefire Redteam to resemble the actions of actual adversaries. The natural attack progression seen in contemporary financial intrusions is depicted in the flow below.
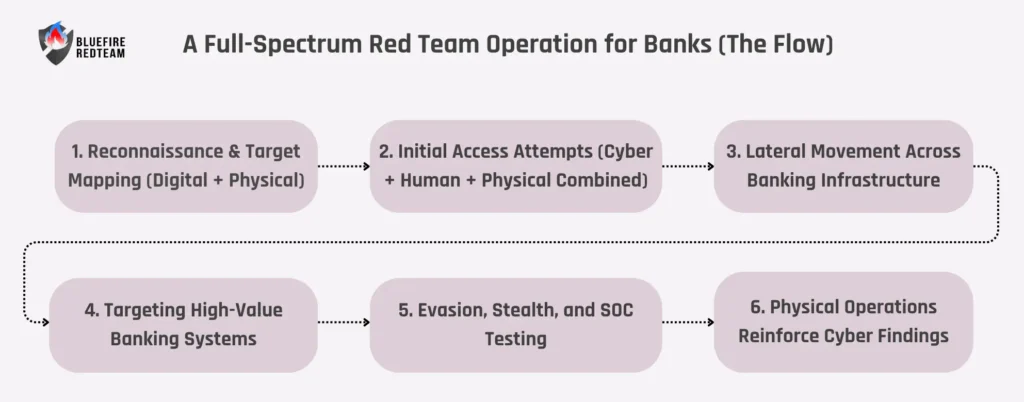
1. Reconnaissance & Target Mapping (Digital + Physical)
The operation begins by understanding:
- Employee roles
- Branch locations
- Vendor access paths
- Cloud tenants
- Exposed services
- Physical security checkpoints
Attackers combine OSINT, social media, physical observation, and digital footprint analysis to build a complete picture.
2. Initial Access Attempts (Cyber + Human + Physical Combined)
Most real attacks start with one of three entry points:
Cyber Access
- Spear-phishing
- MFA fatigue
- Cloud identity brute force
- VPN/Citrix exploits
- Supply-chain access
Social Engineering Access
- Impersonation of vendors or technicians
- Fake HR outreach
- Rogue contractor pretexts
- Executive impersonation
Physical Access (critical for banking environments)
- Tailgating at branch offices
- Badge cloning from staff
- Gaining entry as a “maintenance worker”
- Accessing unattended workstations
- Exploiting reception desk weaknesses
For banks, physical entry is just as valuable as cyber compromise because a single exposed port or unlocked device can provide immediate high-privilege access.
Bluefire tests all three vectors simultaneously — as real attackers would.
3. Lateral Movement Across Banking Infrastructure
Once inside (physically or digitally), attackers attempt to escalate and move:
- Harvesting credentials
- Token impersonation
- Kerberos attacks
- Bypassing EDR/SIEM detections
- Moving toward core banking systems
- Investigating SWIFT-related segments
- Identifying privileged administrative accounts
Physical access often accelerates lateral movement:
For example, a rogue device planted inside a branch can pivot into internal systems far more easily than an external attacker.
This is why banks must test combined attack paths, not isolated security layers.
4. Targeting High-Value Banking Systems
Bluefire’s scenarios reflect the real objectives attackers pursue:
- Payment processing manipulation
- Account takeover
- SWIFT system exploration
- Access to financial applications
- Manipulation of transaction workflows
- Exposure of core banking data
These objectives reveal whether a bank can withstand true financial-grade adversaries.
5. Evasion, Stealth, and SOC Testing
In a real intrusion, attackers avoid detection for weeks or months.
Bluefire measures:
- How long attackers remain undetected (dwell time)
- Whether the SOC identifies unusual lateral movement
- If alerts trigger at the right time
- Whether escalations occur properly
- How well responders coordinate with IT and business units
This is the heart of operational resilience.
6. Physical Operations Reinforce Cyber Findings
Physical Red Teaming is woven throughout the engagement flow — not treated as a separate session.
Examples:
- Physical entry reveals weaknesses in branch processes
- Rogue device placement enables internal pivoting
- Tailgating leads to access to privileged workstations
- Social engineering unlocks accounts or privileged systems
- Physical badge compromise leads to secure floor access
The lesson for banks:
Attackers don’t respect boundaries between cyber, human, and physical domains — so your Red Teaming shouldn’t either.
Regulatory Alignment (In a Single Integrated Flow)
Bluefire Redteam’s engagements naturally support financial regulatory frameworks by following the holistic attacker journey.
BaFin (BAIT & VAIT)
Requires operational resilience across IT, processes, and physical security.
Red Teaming validates all three live.
TIBER-EU
Explicitly calls for:
- Threat Intel-driven scenarios
- Multi-vector attacks
- Physical entry attempts
- Close collaboration with a White Team
Bluefire’s flow aligns seamlessly with TIBER methodology.
ECB / EBA Guidance
Focuses on resilience beyond IT — including people and facilities.
Bluefire’s integrated model delivers this.
NIS2 (Critical Infrastructure)
Banks must demonstrate capability to handle cyber, physical, and hybrid threats.
Bluefire’s engagements naturally check all boxes.
Why Banks Choose Bluefire Redteam
1. Realistic Multi-Vector Operations
Banks don’t suffer isolated cyber incidents.
They suffer blended attacks.
Bluefire simulates blended attacks end-to-end, including physical entry when relevant.
2. Senior Operators Only
Experts in:
- Payment systems
- Cloud identity
- Physical penetration
- Social engineering
- Detection evasion
- Malware development
No junior analysts. Only elite operators.
3. Deep Banking Experience
Bluefire understands:
- Branch operations
- SWIFT flows
- Payment processes
- Secure floors
- OT inside branches (ATMs, kiosks)
- Hybrid architecture typical of financial institutions
This creates more accurate attack modeling.
4. Cloud + Physical + Cyber Expertise Combined
This combination is rare — and essential.
Most competitors offer one or two layers.
Bluefire delivers all three in a single, coherent operation.
5. Reporting That Banks Can Actually Use
Executives and security teams receive:
- Timeline of attack
- MITRE ATT&CK mapping
- Impact analysis
- Detection & alerting gaps
- Remediation roadmap
Boards and BaFin auditors appreciate the clarity.

What Banks Gain From Full-Spectrum Red Teaming
- A unified view of cyber, human, and physical weaknesses
- Validation of incident response and SOC performance
- High-value insights for BaFin, ECB, and NIS2 compliance
- Prioritization of the most impactful remediation steps
- Stronger cloud identity and hybrid security posture
- Improved physical security processes at branches and HQ
- Real understanding of business risk
Request a Full-Spectrum Red Teaming Proposal for Your Bank
If your bank needs:
- Real adversary simulation
- Cyber + social + physical attack testing
- BaFin / TIBER-EU aligned exercises
- Cloud and on-premise attack coverage
- Trusted senior operators
Then Bluefire Redteam is your ideal partner.


