One of the best methods to make sure your application is resilient to real-world attacks is to conduct web application penetration testing.
With cyberattacks on web applications increasing by 67% in the past year, securing your digital assets is no longer optional — it’s essential
In this manual, we will discuss:
- What it is
- Why it’s important
- The process
- When to do it
- How to choose a provider
What is web application penetration testing?
Web application penetration testing is a controlled, simulated cyberattack on a web application, performed by ethical hackers.
Its goal is to identify, exploit, and report vulnerabilities before malicious actors can.
Pentesting goes deeper than simple vulnerability scanning, determining whether vulnerabilities can be exploited and evaluating their actual business impact.
Why Web Application Penetration Testing Matters
- Prevent Data Breaches
Detect and fix weaknesses before attackers exploit them. - Meet Compliance Requirements
Frameworks like PCI DSS, HIPAA, SOC 2 often require regular penetration testing. - Protect Brand Reputation
A single breach can damage customer trust for years. - Improve Security Posture
Understand and strengthen your defenses over time.
Common Vulnerabilities Found
During a typical test, security professionals look for:
- SQL Injection
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- Broken Authentication
- Insecure Direct Object References
- Security Misconfigurations
- Business Logic Flaws
The Web Application Penetration Testing Process
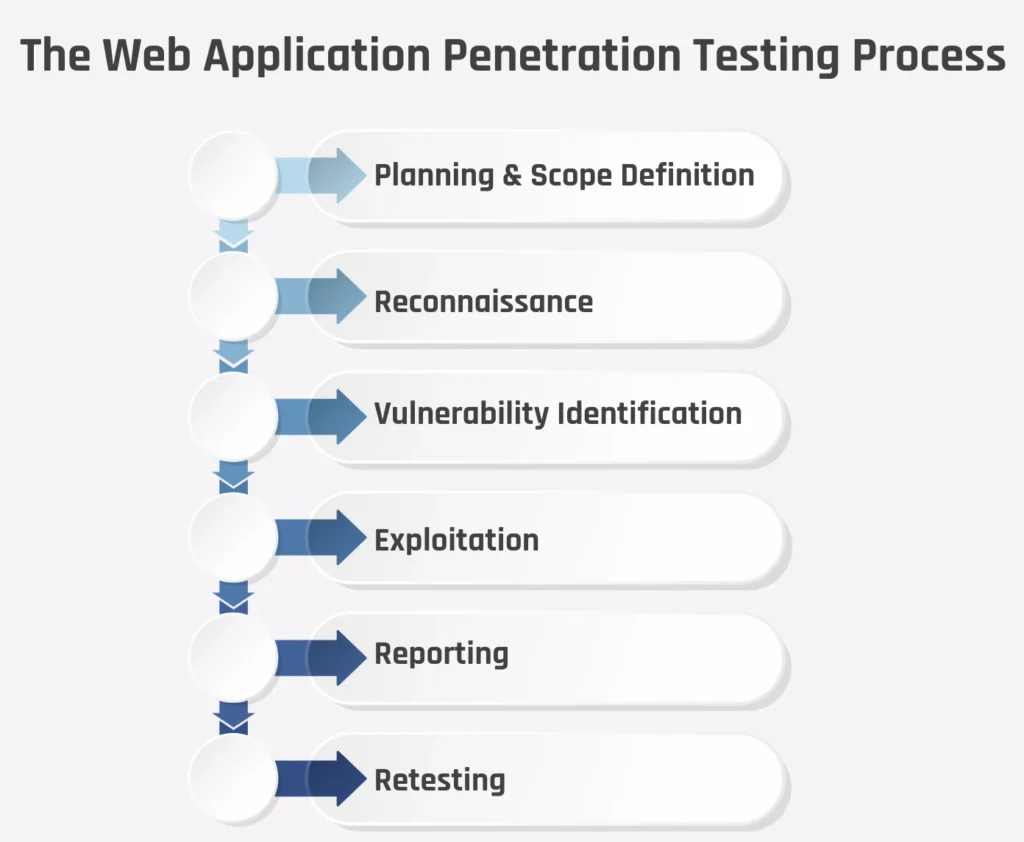
- Planning & Scope Definition
Identify the parameters, test boundaries, and target URLs. - Reconnaissance
Learn about the technologies, frameworks, and structure of the app. - Vulnerability Identification
To find flaws, use both automated tools and manual probing. - Exploitation
To determine the impact, try to exploit vulnerabilities. - Reporting
Deliver a detailed report with severity ratings and remediation guidance. - Retesting
Verify that vulnerabilities have been successfully patched.
When to Perform a Web Application Penetration Test
- Before launching a new application
- After significant code changes
- At least annually for compliance
- After a security incident
Manual vs Automated Testing
Automated scans are fast and cost-effective, but may miss complex vulnerabilities.
Manual testing, done by skilled security professionals, provides deeper coverage and detects business logic flaws.
Best practice: Use both for comprehensive security.
Read our full guide: Manual vs Automated Web Application Penetration Testing →
Choosing the Right Provider
Look for:
- Industry Experience — Knowledge of your sector’s threats and regulations.
- Certifications — OSCP, CREST, GPEN.
- Methodology — OWASP Top 10, NIST standards.
- Clear Reporting — Executive summaries + technical details.
- Remediation Support — Assistance fixing vulnerabilities.
Bluefire Redteam: Your Web Application Security Partner
Web application penetration testing for businesses, SaaS providers, fintech companies, and healthcare institutions is our area of expertise at Bluefire Redteam.
Our blend of manual expertise and automated scanning ensures vulnerabilities are found and fixed before they become a problem.
Schedule Your Web Application Security Assessment →
FAQ – Web Application Penetration Testing
- What is web application penetration testing?Web application penetration testing is a simulated cyberattack on a web app to find and exploit vulnerabilities before real attackers do. It identifies flaws like SQL injection, XSS, CSRF, authentication bypass, and logic errors.
- Why is web application penetration testing important?
It helps prevent data breaches, ensures compliance with standards like PCI DSS, HIPAA, and SOC 2, and protects brand reputation by proactively addressing security weaknesses.
- How often should I perform web application penetration testing?
At least once per year, and after any major code changes, new feature releases, or security incidents.
- How long does a web application penetration test take?A typical assessment lasts 5–15 business days, depending on application complexity, number of user roles, and testing depth.
- How much does web application penetration testing cost?Prices range from $5,000 to $50,000+ based on scope, size, and industry compliance requirements.
- Does penetration testing disrupt normal operations?No — ethical testers follow safe procedures that won’t damage systems or interrupt regular business activities.
- What’s the difference between web application penetration testing and vulnerability scanning?Vulnerability scanning is automated and finds known weaknesses, while penetration testing uses manual techniques to exploit vulnerabilities, uncover logic flaws, and validate real-world risk.
- Who should conduct my web application penetration testing?Choose certified professionals (OSCP, CREST, GPEN) with proven industry experience and a track record of thorough reporting and remediation support.
- How much does web application penetration testing cost?Pricing usually ranges from $2,000 to $20,000+ depending on the number of applications, complexity, compliance requirements, and whether manual testing is included.