Cyberattacks are now a daily occurrence rather than merely a threat.
- Over 2,200 cyberattacks occur daily, or almost one every 39 seconds.
- Over a three-year period, the average cost of a data breach increased by 15% to $4.45 million in 2023.
- In 82% of breaches, exploited vulnerabilities or human error were the cause.
- Nevertheless, 43% of SMBs continue to function without a formal cybersecurity plan.
In the connected world of today, your entire company could be at risk from a single weak point. Vulnerability Assessment and Penetration Testing (VAPT) becomes essential in this situation.
In this blog post, we will explore VAPT, how a buyer should consider and how it’s done.
What is VAPT Testing?
Two separate but complementary cybersecurity practices are combined to form VAPT:
- Vulnerability Assessment (VA): A thorough examination of systems to find known weaknesses.
- A simulated cyberattack used to actively exploit vulnerabilities and evaluate the possible impact is known as penetration testing, or PT.
From surface-level vulnerabilities to exploitable flaws, this dual approach gives organisations a comprehensive picture of their security posture.
VAPT vs. Other Security Testing Methods
Here’s how VAPT compares with other popular cybersecurity practices:
| Method | Purpose | Depth of Coverage | Real-World Exploitation | Best Use Case |
| VAPT (VA + PT) Testing | Identify & exploit vulnerabilities in systems/apps | Deep (tech + logic flaws) | Yes | Comprehensive risk discovery & validation |
| Bug Bounty Programs | Crowdsource real hackers to find bugs | Depends on bounty scope | Yes | Public apps with mature security posture |
| Automated Vulnerability Scanning | Detect known CVEs using tools | Surface-level | No | Quick checks, compliance snapshots |
| Static Application Security Testing (SAST) | Scan source code for security flaws (at rest) | Code-level only | No | Secure code review during development |
| Dynamic Application Security Testing (DAST) | Test running applications for security issues | Runtime issues only | No | Scan live environments during QA/staging |
| Red Teaming | Simulate targeted, stealthy APT-style attacks | Very deep, adversarial | Yes |
The VAPT Process Explained
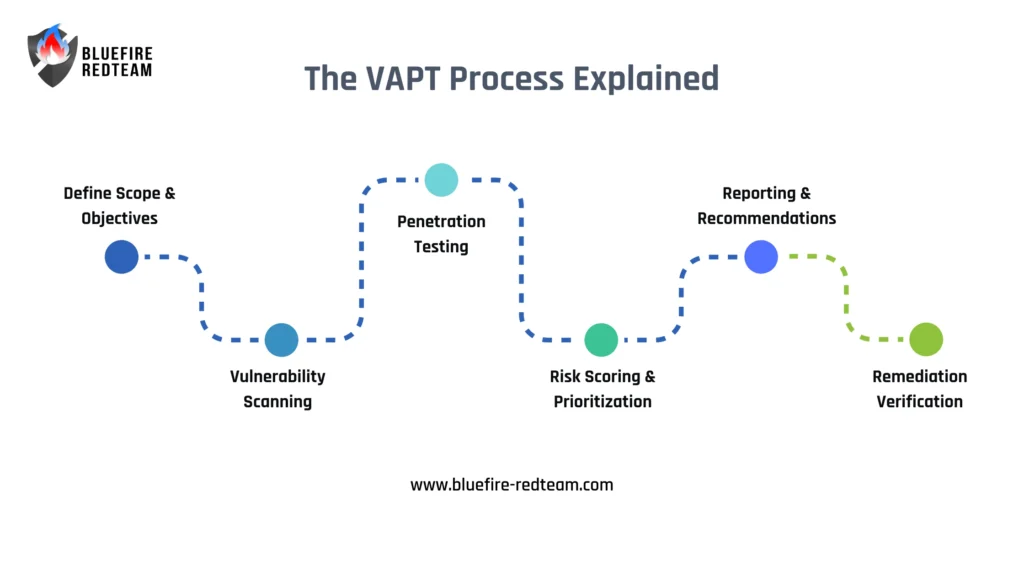
1. Define Scope & Objectives
Determine which networks, apps, and systems will be tested. Add the needs for compliance and business objectives.
2. Vulnerability Scanning
Systems are scanned for known vulnerabilities using both automated and manual tools.
3. Penetration Testing
Certified experts simulate real-world attacks to test how vulnerabilities can be exploited.
4. Risk Scoring & Prioritisation
Findings are ranked according to exploitability, impact, and asset exposuer using industry frameworks such as CVSS, and we use our in-house prioritisation process as well.
5. Reporting & Recommendations
Receive a detailed report including:
- Vulnerability details
- Proof-of-Concept (PoC) evidence
- Business impact
- Suggested remediation steps
6. Remediation Verification
We re-test after fixes are implemented to confirm their efficacy.
When Do You Need VAPT Testing?
Top Scenarios That Demand Vulnerability Assessment and Penetration Testing
Vulnerability Assessment and Penetration Testing (VAPT) isn’t just a one-time checkbox—it’s a critical security measure that should be integrated into your IT and DevSecOps lifecycle. Here’s when your organisation should prioritise VAPT:
1. Launching New Applications, APIs, or Websites
VAPT helps make sure you’re not exposing your company to known or unknown vulnerabilities before launching any digital product, be it a customer portal, mobile app, or API gateway.
Why? Security Flaws such as compromised authentication, unsafe API endpoints, or exposed private information are found early in the testing process.
2. After Infrastructure or Codebase Changes
Risks increase with any change to your environment, including cloud migration, tech stack upgrades, new integrations, and infrastructure reorganisation.
Why? Serious security gaps can be introduced by even small changes. VAPT assists in identifying those before attackers do.
3. To Meet Compliance & Regulatory Requirements
Regular security assessments are required by frameworks such as ISO 27001, GDPR, HIPAA, PCI-DSS, and SOC 2 to verify system integrity and guarantee the protection of customer data.
Why? VAPT offers the risk analysis and audit-ready documentation required to meet compliance requirements.
4. Following an incident or security breach
A VAPT engagement can help you understand your exposure and stop further exploitation if your company has been the victim of a phishing attack, malware infection, or data breach.
Why? Remaining backdoors, incorrect configurations, or vulnerabilities overlooked during cleanup are discovered through post-event testing.
5. As a component of routine cybersecurity hygiene (either quarterly or annually)
Security threats are always changing, even in the absence of significant changes. Your defences will always be current if you follow a proactive VAPT schedule.
Why? Regular VAPT helps keep ahead of newly discovered vulnerabilities (such as Log4j or zero-day exploits).
BONUS: Before Partnering with Vendors or Clients
Nowadays, a lot of business partners and clients demand security validation before conducting business. Doing a VAPT can help you win deals and build trust.
Why? You have a competitive edge in business-to-business interactions when you exhibit a secure posture.
How to Choose the Right VAPT Testing Provider
Key Factors to Evaluate Before You Commit
Choosing the best Vulnerability Assessment and Penetration Testing (VAPT) provider involves more than just verifying technical credentials; it also involves putting your trust in someone to securely mimic actual attacks on your most important assets. What to look for is as follows:
1. OSCP & Other Industry Certified Experts
Credentials accepted by the industry attest to your provider’s technical proficiency and moral character.
OSCP and other industry-certified penetration testers with practical offensive security experience work for Bluefire Redteam.
2. Manual Testing Capabilities
Business logic bypasses and logic-based security flaws cannot be found by automated scans alone. Seek out a team that uses both manual testing and automation.
For thorough coverage, we employ a hybrid strategy that combines manual testing with proprietary tools.
3. Controlled Intrusion Methodology
Your provider must approach exploitation in a controlled and non-destructive manner. This guarantees that testing won’t interfere with services or cause actual harm.
Bluefire Redteam uses “controlled intrusion” techniques, which replicate actual threats without endangering your systems. Each test has a strict scope, documentation, and prior approval.
Our approach is tried and tested in over 300 VAPT engagements.

4. Clear, Actionable Remediation Guidance
A quality VAPT provider assists you in resolving problems rather than merely identifying them. Request specific technical remediation assistance rather than general recommendations.
Our reports contain architecture-level recommendations, developer guidance, and remediation steps that are prioritised.
5. Post-Remediation Testing
After the report, security doesn’t stop. Select a partner who verifies your fixes and makes sure there are no regression vulnerabilities.
We offer one round of re-testing for free after remediation.
6. PTaaS & Ongoing Support
For smooth integration, your provider should provide Penetration Testing as a Service (PTaaS) if your company needs continuous security testing (CI/CD, DevSecOps).
Our PTaaS platform lets you monitor vulnerabilities in real time, track remediation, and collaborate with your teams efficiently.
Why Choose Bluefire Redteam for VAPT Testing Services?
Selecting the appropriate cybersecurity partner is crucial for protecting your digital infrastructure. At Bluefire Redteam, we provide full-spectrum, real-world VAPT services that shield your company from the most advanced cyberthreats of today, going beyond conventional penetration testing.
Here’s why organisations across industries trust Bluefire Redteam:
A track record of success across industries
We have successfully provided VAPT services to healthcare organisations, SaaS startups, banking and finance companies, and e-commerce businesses.
Benefit: We provide customised assessments that fit your risk environment because we are aware of the distinct threat models and compliance needs of every industry.
Look what our customer said about us:

Read their full verified review
Elite Red Team Members with Practical Experience
The professionals on our team are certified in OSCP, CREST and have practical experience in advanced threat simulation, offensive security, and red teaming.
Benefit: Working with ethical hackers who mimic actual breach scenarios and think like real adversaries is more beneficial than simply hiring testers.
Realistic Attack Simulations Mapped to MITRE ATT&CK
We map all penetration testing activities to the MITRE ATT&CK framework, ensuring your VAPT report aligns with the latest attacker tactics, techniques, and procedures (TTPs).
Benefit: This gives your security team a better understanding of how attackers might move through your network—and how to stop them.
Comprehensive Vulnerability Lifecycle Management
We handle the entire lifecycle of your vulnerabilities, from identification and exploitation to thorough reporting, remediation advice, and post-fix validation.
Benefit: We assist your team in swiftly and efficiently addressing security flaws, so you’re not left wondering what to fix or how to fix it.
Full-Stack Security Testing: Web, Mobile, API, Cloud, and Internal Infrastructure
Our VAPT methodology spans all layers of your digital environment, including:
- Web Application Penetration Testing
- Mobile App Security Testing (iOS & Android)
- API Security Testing
- Cloud Infrastructure Security (AWS, Azure, GCP)
- Internal and External Network Infrastructure Testing
Benefit: One knowledgeable team that can evaluate your whole technology stack, making sure that no weak point is overlooked.
Learn more about our VAPT Testing Services.
Top Award-winning VAPT Testing Provider Company
Time and again, we are recognised as the top VAPT Provider.
Why This Matters: When you work with an award-winning team, you’re choosing a VAPT partner that’s battle-tested, industry-validated, and dedicated to setting the standard for offensive security.

Bonus: Transparent Reporting + Executive Dashboards
We blend executive clarity with technical depth. While our dashboards make it simple for CISOs and CTOs to monitor remediation progress and risk posture over time, our reports are sufficiently detailed for developers and auditors.
Introducing PentestLive – Track vulnerabilities in real-time.
Watch this short video to learn more:
Real-World Case Study on VAPT Testing

One of the top international innovators in healthcare solutions reached out to us with an urgent issue: protecting their digital infrastructure. Their operations revolve around patient and physician data, so they understood how critical it was to protect sensitive data from online attacks.
Challenge
They encountered serious cybersecurity issues with both their mobile and web apps. These flaws presented compliance issues in addition to endangering user data. The client needed to strengthen their defences in order to preserve credibility and trust as regulatory scrutiny increased.
Solution
Our team carefully examined the client’s digital assets in order to address their security concerns. We identified vulnerabilities and created a defence roadmap by combining our manual expertise with cutting-edge tools. Our investigation revealed a number of vulnerabilities, all of which need to be fixed right away.
Conclusion
VAPT ought to be on your roadmap if you’re developing, expanding, or safeguarding any digital system. With transparent reporting, doable corrective actions, and quantifiable risk mitigation, Bluefire Redteam assists you in doing it correctly.
Contact us now to schedule your VAPT Testing engagement.
Frequently Asked Questions(FAQs) - VAPT
- What is VAPT and why is it important?Vulnerability Assessment and Penetration Testing is referred to as VAPT. It assists companies in locating and addressing security vulnerabilities before hackers take advantage of them. It is essential for safeguarding private information, guaranteeing adherence to regulations (such as PCI, HIPAA, and SOC 2), and enhancing overall cyber resilience.
- How do I choose the right VAPT company?Seek out businesses with a track record of success in the field, certified security professionals (such as OSCP or CISSP), adaptable testing methodologies, and transparent reporting. Make sure they provide post-testing assistance as well, such as remediation advice and retesting.
- How much does VAPT cost?Depending on the scope (web app, cloud, mobile, internal network), depth of testing, and complexity of systems, VAPT costs normally range from $1,000 to more than $10,000. Additionally, some providers provide continuous testing that is subscription-based.
- What’s the difference between Vulnerability Assessment and Penetration Testing?Vulnerability assessment uses automated scans to find known security flaws. To exploit those flaws and determine the true risk, penetration testing mimics actual attacks. Both are combined by VAPT to provide a more comprehensive security picture.
- Do small businesses need VAPT?Of course. Because they have fewer security measures in place, cyberattacks are increasingly targeting small businesses. VAPT safeguards consumer data, fosters trust with partners, clients, and regulators, and assists in identifying hidden vulnerabilities early.


