Cloud infrastructure has changed how companies grow, but it has also created new risks and attack points.
Given that AWS powers everything from government workloads to e-commerce, it should come as no surprise that attackers target it frequently.
AWS penetration testing is how leading security teams proactively find misconfigurations and weaknesses—before real attackers do.
In this guide, we break down what AWS pentesting involves, what you’re allowed to test, and how to ensure your cloud environment is secure.

What Is AWS Penetration Testing?
AWS penetration testing is the process of simulating real-world cyberattacks on your Amazon Web Services environment.
Penetration testing uses manual exploitation to determine how an attacker could actually obtain access or move laterally within your cloud infrastructure, in contrast to vulnerability scanning, which looks for known problems.
Key Targets May Include:
- EC2 Instances (virtual machines)
- S3 Buckets (object storage)
- IAM Roles & Policies (identity access)
- Lambda Functions (serverless workloads)
- RDS Databases
- CloudFront & API Gateways
✅ It’s designed to answer: “What would happen if an attacker breached this AWS account?”
Is AWS Penetration Testing Allowed?
Yes—AWS allows penetration testing of most of its services, but there are rules you must follow.
📌 The majority of AWS pentests no longer require prior authorisation as of 2019.
✅ Services You Can Test Without Approval:
- EC2, RDS, CloudFront
- Lambda functions
- API Gateway
- Elastic Beanstalk
- Lightsail
- Aurora
❌ What’s Prohibited:
- Denial of Service (DoS) or DDoS
- DNS zone walking
- Port flooding or protocol abuse
- Tests that affect other AWS customers
📖 Full AWS Pentesting Policy →
Why AWS Environments Are High-Value Targets
Even big businesses with teams that are cloud-native make expensive errors that hackers take advantage of.
Common missteps include:
- Public S3 buckets exposing sensitive data
- Over-permissive IAM roles with admin access
- APIs with no authentication
- Secrets (API keys, credentials) hardcoded in environment variables or Lambda functions
💡 Bluefire’s Insight:
“Most cloud breaches are not zero-days—they’re misconfigurations hiding in plain sight.”
What a Good AWS Pen Test Includes
At Bluefire Redteam, an effective AWS pentest goes far beyond scanning.
Here’s what we cover:
- Enumeration: Identifying active services, roles, assets
- IAM Abuse: Testing privilege escalation via weak permissions
- S3 & EBS Audits: Searching for exposed storage and snapshots
- Credential Leaks: Testing Lambda, ECS, and user data exposures
- Lateral Movement: Attempting cross-service pivoting
- Persistence & Reporting: Documenting how an attacker could maintain access undetected
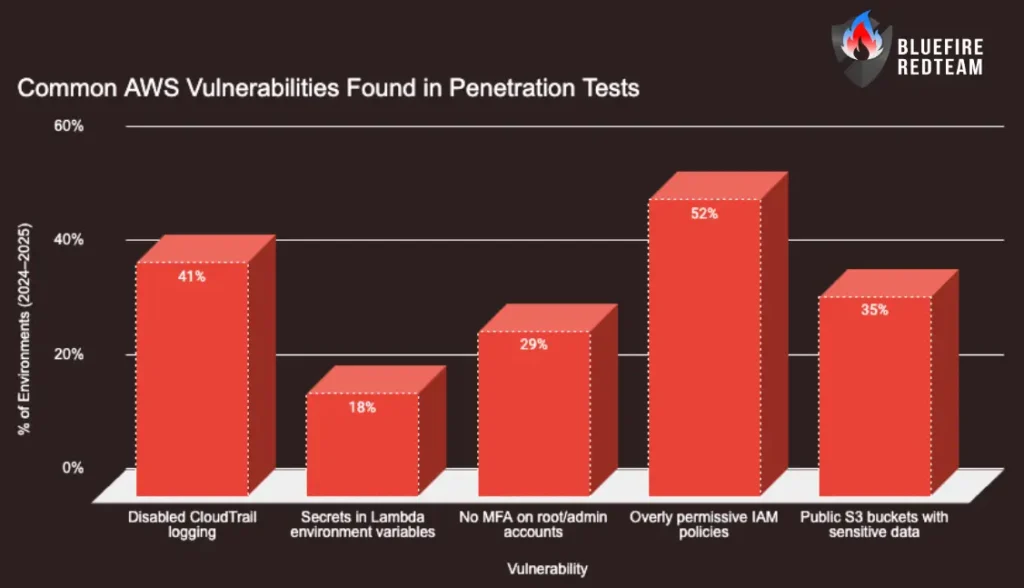
Common AWS Vulnerabilities Found in Penetration Tests
Even mature AWS environments often reveal these issues:
How Often Should You Pentest Your AWS Environment?
There’s no one-size-fits-all—but here’s our expert guidance:
| Environment Type | Recommended Frequency |
|---|---|
| Dev/Test | Annually or before major launches |
| Production | Quarterly or biannually |
| Regulated (SOC 2, ISO) | At least annually |
| High-risk workloads | Quarterly or on major change |
💡 Frequent updates or CI/CD pipelines? Consider ongoing assessments or bug bounty models.
Choosing the Right AWS Pentesting Partner
Not all pentesters are cloud-literate. Look for firms with:
- Demonstrated track record of AWS pentests
- Red team capabilities and mimicry of adversaries
- Knowledge of Lambda, KMS, EKS, IAM, etc.
- Post-engagement support & remediation guidance
Why Bluefire Redteam?
We’ve tested everything from startup workloads to enterprise cloud environments—and we tailor every engagement to simulate real-world cloud threat actors. Reach out to know more about our layered approach for AWS penetration testing.
Conclusion: Secure the Cloud Before They Do
AWS penetration testing is no longer optional—it’s a foundational part of any modern security program.
Done right, it reveals the exact paths attackers could take—and helps your team close them before it costs you data, downtime, or dollars.
👉 Schedule an AWS Penetration Testing Now!
References
- AWS Penetration Testing Policy
- OWASP Cloud Security Guidelines
- CISA Cloud Security Tips
- Bluefire Redteam Engagement Data (2024–2025)


