In 2025, ransomware had developed into a formalized criminal economy. What used to appear to be disorganized malware outbreaks now looks more like planned operations with revenue targets, supply chains, and specialized job roles. Attackers are more well-funded, more strategic, and concentrate on the three things that hurt businesses the most: availability, identity, and data.
In this comprehensive report, we break down the latest ransomware statistics, top attack vectors, industry impact patterns, and what organizations can do to prepare, based on data aggregated from Coveware, Chainalysis, Recorded Future, ENISA, and ongoing internal incident response and red teaming work by Bluefire Redteam.
CISOs, security architects, blue teams, incident responders, and risk owners in charge of business continuity and cyber defense plans are the target audience for this guide.

Ransomware in 2025: Key Statistics at a Glance
| Metric | 2024 | 2025 (YTD) | Trend and Notes |
|---|---|---|---|
| Average Ransom Demand | $740,000 | $1.4 million | Attackers are choosing high-value victims rather than large volumes. |
| Average Ransom Paid | $275,000 | $640,000 | Negotiation leverage shifting in favor of attackers. |
| Median Downtime After Attack | 7 days | 14 to 21 days | Recovery complexity continues to increase. |
| Cases Involving Data Theft (Not Encryption) | 36% | 52% | Extortion-only attacks outpaced encryption attacks for the first time. |
| Cases Involving Triple Extortion (data theft + encryption + contacting customers/partners) | 9% | 22% | Public relations pressure has become an attack tool. |

Why the Shift?
In previous years, ransomware relied on encryption. Organizations responded by improving backups and disaster recovery. Attackers adapted.
In 2025, the real threat is not encryption. It is exposure.
Attackers now:
- Steal data before encrypting.
- Threaten public leaks on dedicated leak sites.
- Contact customers, board members, or media to increase pressure.
The core assumption has changed:
“Backups recover files” does not protect from extortion.
Industries Most Targeted in 2025
| Industry | Reason for Targeting | Impact Profile |
|---|---|---|
| Healthcare | Urgency and patient care downtime pressure | High likelihood of ransom payment |
| Energy and Utilities | Heavy operational dependency | Regulatory and national security implications |
| Manufacturing and Logistics | Sensitive supply chain continuity | Disruption causes cascading economic loss |
| Financial Services | High data sensitivity and transaction continuity | Data theft is more damaging than downtime |
Ransomware actors focus on business models where interruption is intolerable.
Top Ransomware Groups Operating in 2025
| Group Name | Characteristics | Primary Entry Method |
|---|---|---|
| Qilin | Data extortion dominant, aggressive leak pressure | Exposed RDP and weak credential reuse |
| LockBit Reborn | Reorganized affiliate network after takedowns | Compromised VPN and legacy AD paths |
| Akira | Highly methodical negotiation playbook | Phishing and initial access brokers |
| Black Basta | Fast lateral movement, focuses on endpoint compromise | Insecure domain controllers and misconfigured EDR |
These groups now operate more like platforms than gangs. They provide:
- Malware frameworks
- Playbooks
- Recruitment channels for affiliates
- Cryptocurrency laundering and profit-sharing
This is why “arresting one hacker” no longer disrupts operations.

How Organizations Are Actually Getting Breached
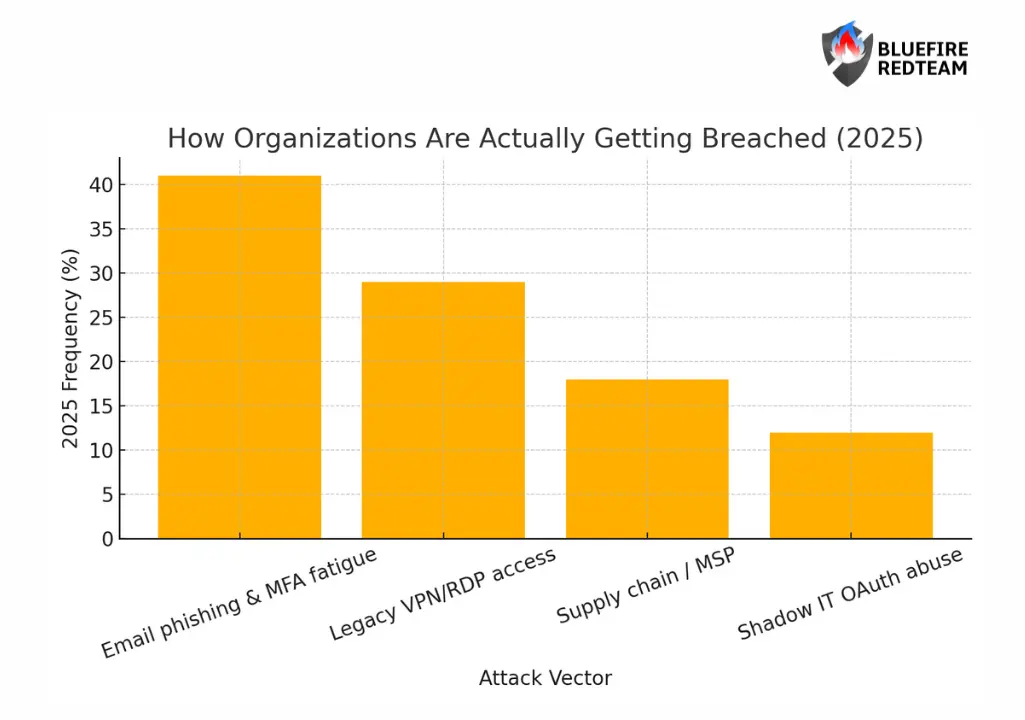
| Attack Vector | 2025 Frequency | Key Detail |
|---|---|---|
| Email phishing and MFA fatigue | 41% | Users are the fastest route into identity trust chains. |
| Exposed or legacy VPN/RDP access | 29% | VPN is being replaced by zero trust for a reason. |
| Supply chain / third-party MSP compromise | 18% | Attack one IT provider and breach dozens of clients. |
| Shadow IT SaaS OAuth token abuse | 12% | OAuth access bypasses password and MFA defenses entirely. |
The modern ransomware kill chain is identity-first, not malware-first.
The New Ransomware Attack Lifecycle (2025)
- Initial Entry
Social engineering, credential theft, VPN access, OAuth token hijack. - Internal Reconnaissance
Mapping identity, access policy, cloud control planes, AD trust flow. - Privilege Escalation
Token theft, Kerberoasting, session hijacking, EDR evasion. - Data Collection and Exfiltration
Data is systematically identified by business value, not size. - Ransom Phase
Threats include:- Public leak
- Contacting customers
- Legal exposure
- Regulatory breach notifications
- Encryption of systems (optional)
This is coordinated, patient, and methodical.
What CISOs Should Do to Prepare in 2025
A defense strategy centered only on firewalls and backups will fail.
The resilience model now centers on Identity, Least Privilege, and Recovery Playbooks.
1. Strengthen Identity Access
- Enforce phishing-resistant MFA
- Remove legacy authentication protocols
- Rotate long-lived tokens regularly
2. Reduce Lateral Movement Paths
- Review Active Directory trust paths every quarter
- Apply network segmentation where operations are sensitive
- Limit domain admin usage to break-glass scenarios only
3. Prepare Leadership for Real Crisis Scenarios
Run tabletop ransomware exercises that include:
- Legal
- PR and communications
- Cyber insurance
- Security teams
Without simulation, response is improvisation.
How Bluefire Redteam Helps
Bluefire Redteam specializes in testing realistic ransomware attack readiness, including:
- Ransomware Tabletop Simulations for CISO and executive teams
- Adversary Simulation and Red Teaming focused on identity takeover and lateral movement paths
- Compromise Path Mapping to identify the shortest path from initial access to business-critical systems
Our goal is to show how an attacker would move, not just whether a vulnerability exists.
We can share a 90-second demonstration video of a real-world physical and digital red team operation if you want to see how a real breach plays out.
Conclusion
Ransomware is no longer a malware problem.
It is a business continuity and identity security challenge.
Compared to those that rely on backups and conventional prevention tools, organizations that comprehend their data exposure, practice responses, and validate their defenses through adversary simulation will be better equipped to handle 2025.
Preparation now is significantly less costly than recovery later.


