Introduction: Why Phishing Remains the #1 Attack Vector
Phishing is responsible for more breaches than any other attack vector — including malware, misconfigurations, and zero-days combined.
Why? Because attackers know the truth CISOs hate to admit:
Your people are your perimeter.
And human error can’t be patched.
Phishing Simulation Services allow organizations to safely test employee susceptibility, measure real-world risk, and reveal how quickly an attacker could compromise accounts, spread laterally, or deploy ransomware.
Everything a CISO, Security Manager, or IT Director needs to make an informed purchase decision is covered in this guide.
What Are Phishing Simulation Services?
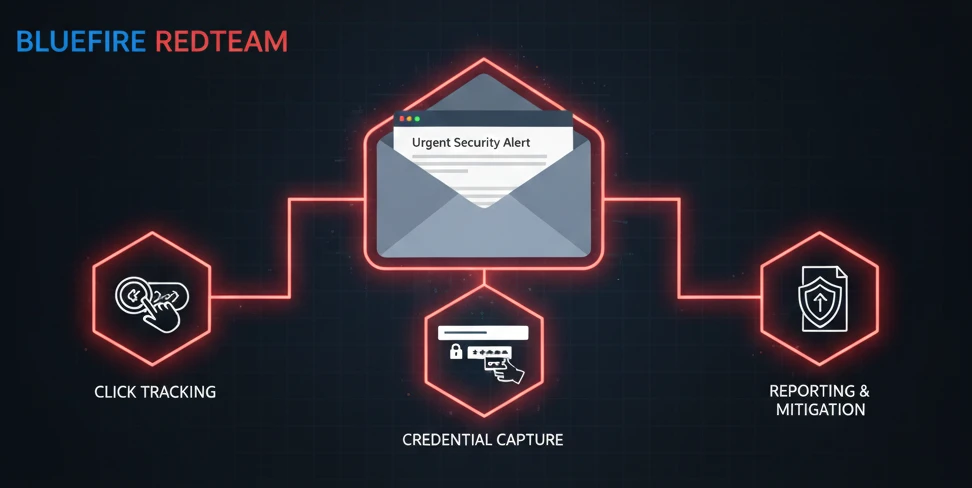
Phishing Simulation Services replicate real-world phishing attacks — without causing harm — to evaluate:
- Employee click rates
- Credential submission rates
- MFA bypass vulnerabilities
- Reporting frequency
- Department vulnerability levels
- Risk reduction over time
Unlike generic “awareness training,” a true phishing simulation:
- Uses real attacker techniques
- Tests behavior, not knowledge
- Measures resilience
- Produces quantifiable risk scores
This is why organizations choose Bluefire Redteam for realistic, adversary-grade simulations.
Types of Phishing Simulations
1. Basic Phishing (Link Click Tests)
Measures who will click suspicious links.
2. Credential Harvesting Simulations
Tests if employees submit passwords.
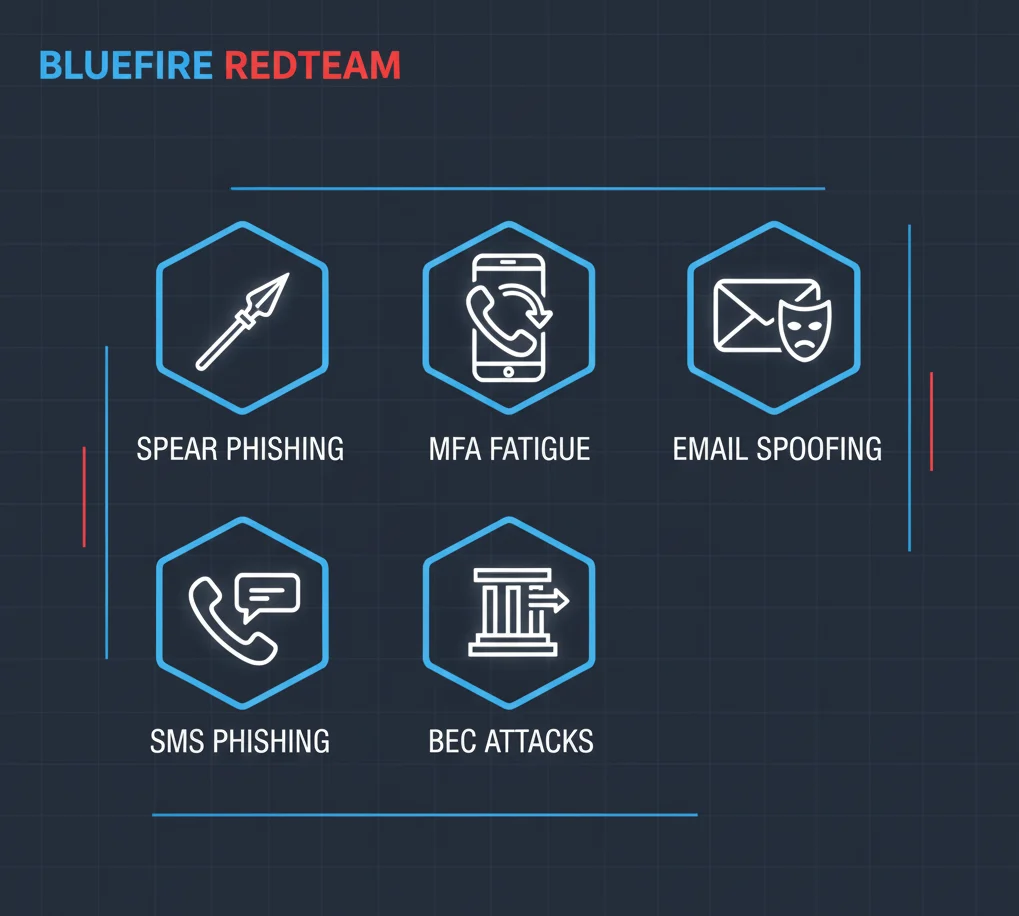
3. Spear Phishing (Highly Personalized)
Targets high-value individuals such as:
- Executives
- Finance teams
- HR
- IT Admins
- Access-provisioning staff
4. Business Email Compromise (BEC) Simulations
Emulates CEO fraud, invoice manipulation, wire-transfer requests.
5. Attachment-Based Phishing
Delivers payload-like attachments (harmless but realistic).
6. MFA Fatigue/Push Bombing Simulations
Tests user response to MFA flooding attacks.
7. OAuth Consent Phishing (Cloud Attack Vector)
Simulates malicious app authorization requests.
8. Vishing & Smishing (Phone/SMS Phishing)
Critical for industries with remote or mobile workforces.
Why Phishing Simulations Are Essential
Modern phishing attacks have evolved dramatically:
- AI-generated emails replicate writing style & tone
- Deepfake voice calls impersonate executives
- Attackers bypass MFA using token theft and push fatigue
- OAuth phishing bypasses passwords entirely
If training is outdated, you lose.
Phishing Simulation Services help identify:
- Risky departments
- Vulnerable employees
- Weak MFA enrollment
- Gaps in detection & response workflows
- Insider threat susceptibility
Attackers adapt — your defenses must too.
Bluefire Redteam’s Phishing Simulation Methodology
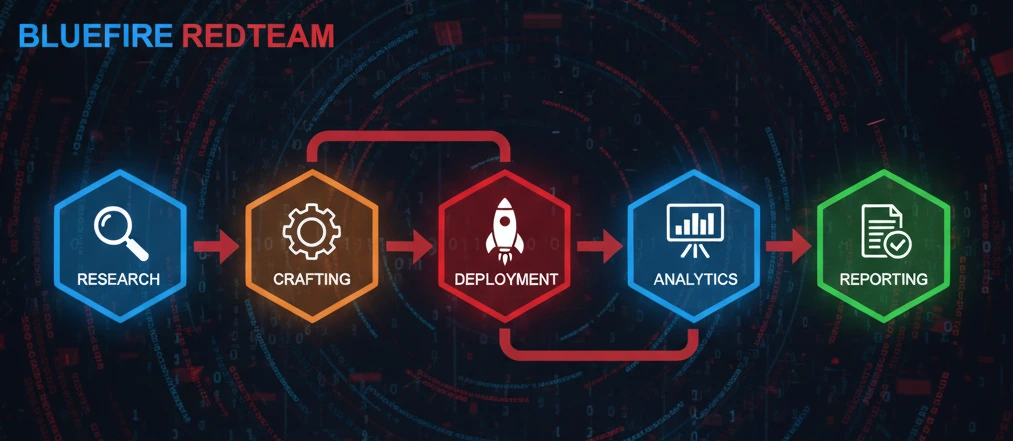
Our approach is not “template-based.”
It’s attacker-driven.
1. Threat Modeling
We identify scenarios attackers would realistically use against your industry.
2. Campaign Development
Custom phishing designs created by offensive security operators.
Examples:
- Cloud login spoofing (Microsoft 365, Google Workspace)
- HR policy notices
- Payment info updates
- Fake vendor onboarding
- Internal file sharing alerts
3. Launch & Monitoring
Campaigns launched over a controlled time window, with tracking of:
- Email opens
- Link clicks
- Credential submissions
- MFA responses
- Reported events
4. Real-Time Insights
We provide live data dashboards showing:
- User-level risk
- Department trends
- Repeat offenders
- Time-to-click metrics
5. Executive & Technical Reporting
Includes:
- Click rates
- Credential submission rates
- Reporting rates
- Recommendations
- Remediation plans
- Behavior improvement benchmarks
6. Retesting
Follow-up campaigns verify improvement (included at no extra cost).
Phishing Simulation Pricing
Phishing simulation costs vary based on your organization’s size, threat exposure, and the realism of the attacks being tested. Instead of fixed pricing, Bluefire Redteam offers customized estimates to ensure you only pay for what you truly need.
Pricing is influenced by:
- Number of users included
- Frequency of campaigns
- Complexity of phishing scenarios
- Need for executive or department-specific targeting
- Reporting depth and analytics
- Add-ons like SMS, voice, or MFA fatigue simulations
Available Pricing Models:
- Per-user pricing for predictable budgeting
- Campaign-based pricing for one-time assessments
- Managed programs for ongoing, adversary-grade simulations
Get an Accurate Quote
Your final investment is tailored to your environment and objectives.
What You Get With Bluefire’s Phishing Simulation Services
You receive:
- Custom phishing scenarios
- Adversary-level TTPs
- Click-through analytics
- Credential capture simulations
- MFA & push fatigue testing
- Reporting & metrics
- Remediation guidance
- Executive summary
- Training recommendations
- Free retesting
This is not entry-level awareness training — it’s professional offensive security.
Who Needs Phishing Simulation Services?
Every organization, but especially:
- Financial institutions
- Healthcare systems
- Government entities
- SaaS companies
- Retail & e-commerce
- Manufacturing
- Education institutes
- Any company with phishing-prone workforce
If email exists, phishing exists.
Why Companies Choose Bluefire Redteam
1. Offense-First Approach
We use the same techniques attackers use — ethically and safely.
2. Custom Campaigns
Not templates. Real adversarial scenarios tailored to your business.
3. Multi-Vector Testing
Email, SMS, voice, MFA fatigue, OAuth phishing.
4. Top-Tier Reporting
Clear metrics, impact analysis, and board-ready summaries.
5. Retesting Included
Security isn’t complete unless verified.
Ready to Strengthen Your Organization Against Phishing?
Bluefire Redteam helps reduce real-world phishing risk with expert-led simulations.


