Oil & gas companies sit at the center of global industrial infrastructure — and they’re also one of the most frequently targeted sectors by nation-state threat actors, ransomware groups, and sophisticated cybercriminals.
With expanding OT/ICS systems, aging equipment, cloud adoption, and complex supply chain dependencies, the attack surface has never been larger.
If you’re considering red team services for oil & gas environments, this guide will walk you through what a real engagement includes, why it matters, and how to evaluate providers who understand both IT and OT realities.
Why Red Teaming Matters in Oil & Gas

Oil & gas operations face unique challenges:
- Highly distributed environments (offshore rigs, pipelines, refineries)
- Legacy ICS/OT systems designed before modern cybersecurity existed
- High operational risks where downtime = millions lost per hour
- Nation-state groups actively targeting critical energy infrastructure
- Third-party vendors with privileged access
- Increasing regulatory pressure (NIST 800-82, IEC 62443, TSA Pipeline Security Guidelines)
Unlike penetration testing—which identifies vulnerabilities—red team operations replicate real adversaries, revealing how attackers might move through IT, pivot to OT, escalate privileges, and attempt to impact operations.
The goal is not “find flaws”…
It’s prove whether real attackers could disrupt production, compromise ICS networks, or evade detection.
Common Adversaries Targeting Oil & Gas

Groups historically focused on oil & gas include:
- APT33, APT34, APT35, APT42 (Iran-based threat clusters)
- TEMP.Veles / Sandworm (Russia-linked operations)
- Ransomware gangs targeting key suppliers and OT via IT
- Threat actors exploiting VPNs, cloud misconfigurations, ageing SCADA systems
These adversaries often use a mix of phishing, supply chain infiltration, cloud privilege abuse, and stealthy lateral movement.
A red team engagement mirrors these exact tradecraft patterns.

What a Red Team Engagement Looks Like for Oil & Gas
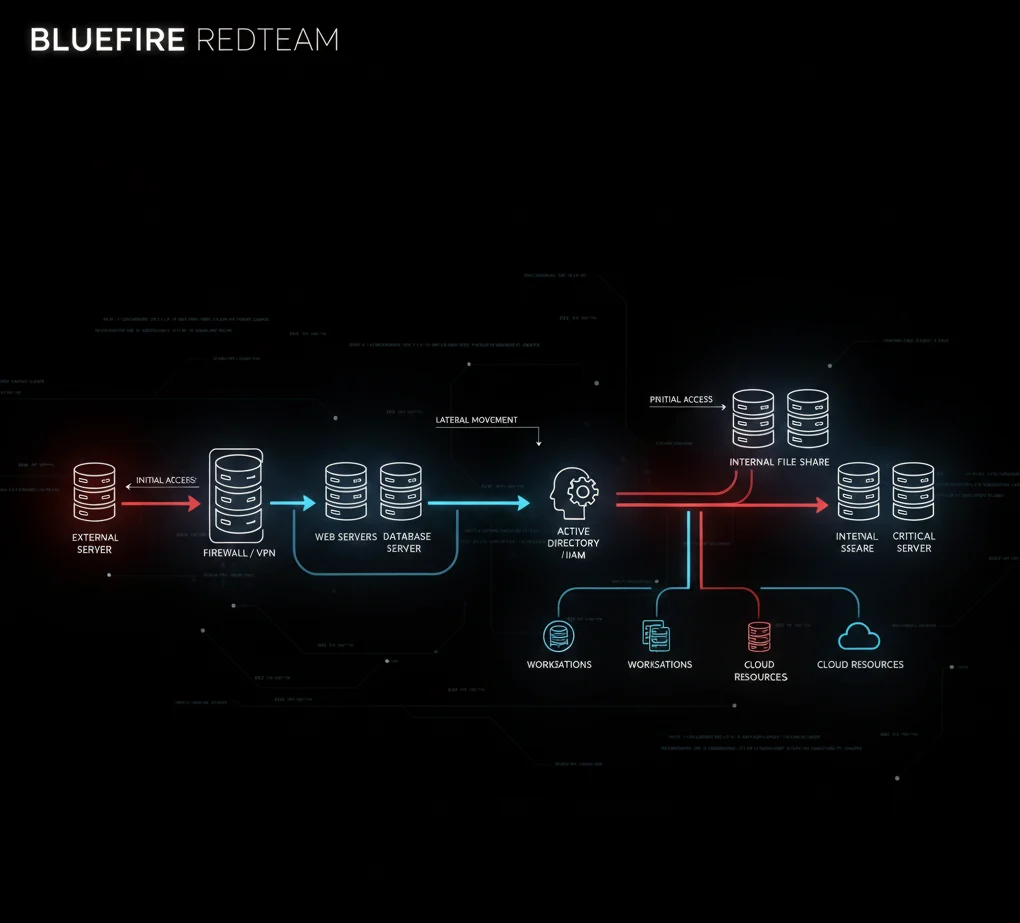
A tailored oil & gas red team assessment usually covers:
1. Initial Access & Foothold
- Spear-phishing attacks
- Exploitation of exposed services
- Stolen or cracked credentials
- Vendor access abuse
2. Internal Network Movement
Once inside, the red team attempts to:
- Enumerate internal networks
- Escalate privileges
- Move laterally
- Identify crown-jewel systems (engineering workstations, historian servers, domain controllers)
3. Cloud & Hybrid Environment Testing
Energy companies increasingly rely on:
- Azure AD
- AWS identity stacks
- Cloud-hosted HMIs
- Remote access portals
Misconfigurations in cloud identity systems are now a major entry point.
4. OT/ICS Reconnaissance — Done Safely
OT testing in oil & gas must follow strict guardrails. Safe activities include:
- Passive discovery
- Reviewing configurations
- Mapping IT-to-OT trust boundaries
- Identifying pivot paths
- Testing segmentation controls
No live testing of PLCs, DCS controllers, or SCADA commands should occur in production environments.
5. Physical & Social Engineering
Because human and physical layers remain exploitable:
- Badge cloning tests
- Tailgating
- Impersonating contractors
- OSINT-based pretexting
- Facility reconnaissance
6. Detection & Response Evaluation
The red team monitors:
- Whether SOC detects intrusion
- Whether OT SOC identifies abnormal behavior
- Whether alerts escalate
- How quickly IR teams respond
- What logging gaps exist
Realistic Scenarios Simulated in Oil & Gas Red Teaming
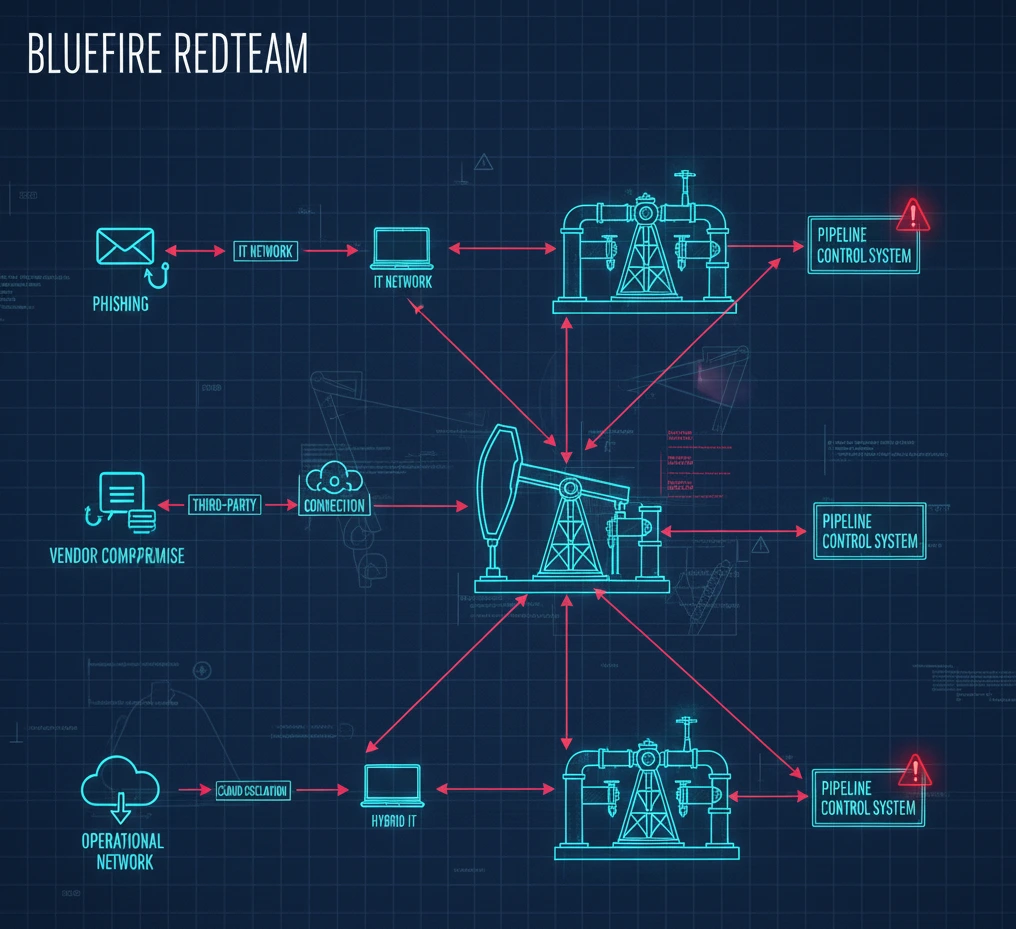
A high-quality engagement includes scenario-based testing. Examples include:
- Ransomware crew attempting domain dominance to impact production scheduling systems
- APT33-like intrusion targeting corporate IT → OT pivot
- Vendor compromise leading to pipeline operations access
- Compromise of engineering workstations used to deploy PLC logic
- Credential theft from remote technicians accessing SCADA via VPN
These simulations help organizations understand realistic attacker paths—not hypothetical ones.
How to Evaluate Red Team Vendors for Oil & Gas
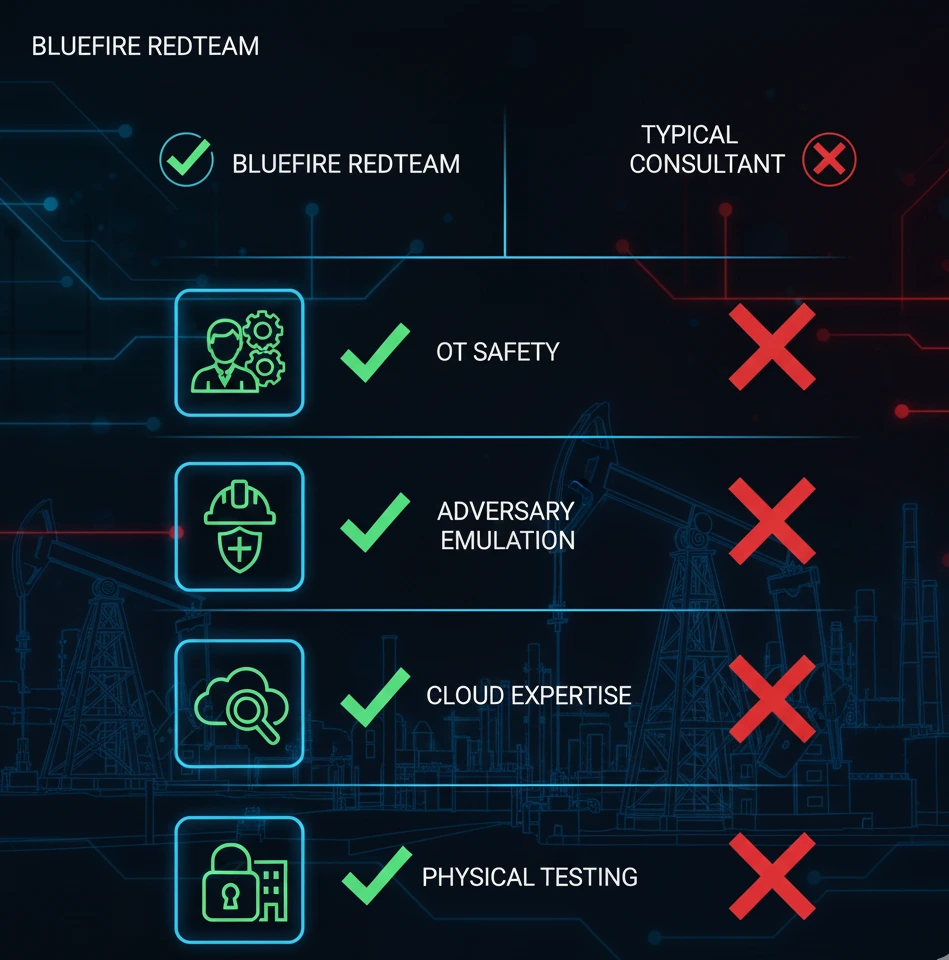
Not all red teams are equipped for ICS-focused industrial environments.
Here’s what you should look for:
Vendor Qualification Criteria
- Documented experience in oil & gas or heavy industrial sectors
- Clear OT safety protocols (no scanning or active payloads in production OT)
- Ability to simulate real adversary TTPs (MITRE ATT&CK + ICS ATT&CK)
- Experience with drilling systems, pipeline SCADA, refinery networks, and DCS architectures
- Hybrid IT + OT operational knowledge
- Cloud identity red team experience (Azure, AWS)
- Physical and social engineering capabilities
- Clear communication with both security and operations teams
- Reporting tailored to engineers, SOC teams, and executives
If a vendor only specializes in corporate IT testing, they may not be equipped for industrial environments.
Red Teaming Challenges Unique to Oil & Gas
1. Safety can’t be compromised.
OT red teaming must be passive.
A real-world attack may damage equipment—your red team partner should never introduce that risk.
2. Many environments still use legacy devices.
Older ICS systems can be fragile.
This requires expertise and extreme caution.
3. Oil & gas networks are sprawling.
From offshore rigs to remote pumping stations, the attack surface is huge.
4. Vendor ecosystems are critical—and risky.
Third-party access is a common attack vector.
Red teams should simulate compromise through contractors.
Expected Outcomes from a Red Team Engagement
When done properly, an engagement gives you:
- A clear picture of how adversaries could enter and move across your environment
- Realistic attack paths from IT → OT
- Visibility gaps preventing early detection
- Weaknesses in identity systems, cloud, and segmentation
- Insights into social engineering risks
- Validation of SOC and OT SOC detection capabilities
- Strengthened IR plans for hybrid industrial environments
- Clear, prioritized remediation steps
The result:
Better operational resilience and reduced risk of catastrophic disruption.
Who Should Consider Red Teaming in Oil & Gas?
Typical teams include:
- CISO & cybersecurity leadership
- OT security managers
- ICS/SCADA engineers
- SOC & IR teams
- Compliance teams (NIST 800-82, TSA, IEC 62443)
- Operational leadership responsible for uptime
Red teaming is most valuable when organizations need to validate:
- Segmentation
- Detection
- Incident response
- Third-party access
- OT exposure
- Cloud attack paths
- Physical security posture
Final Thoughts
Oil & gas companies require more than a generic penetration test.
They need a realistic, safe, adversary-focused assessment that spans corporate IT, cloud, vendors, physical facilities, and OT/ICS networks.
A well-designed red team engagement provides clarity on:
- How attackers would target your environment
- How far they could get
- Whether your teams would detect them
- What defenses must be strengthened
Red teaming is one of the best ways to verify resilience and lower operational risk if your company works in upstream, midstream, or downstream environments.


