New research for security teams. Malvertising and fake browser updates dominated the quarter, but malware notifications across MS-ISAC® monitoring services decreased 18% from Q1 to Q2 2025. With 31% of detections, SocGholish maintained his lead, while ZPHP and Agent Tesla held their positions. ClearFake, Mirai, and NanoCore returned to the chart, while VenomRAT jumped to the #4 position.
Why this matters: In this dataset, malvertising is currently the most common initial access vector. You are at risk if your web controls and endpoint hardening aren’t configured to withstand drive-by payloads that pose as browser updates.
Statistics at a glance
- Quarter‑over‑quarter: Notifications ↓ 18% vs. Q1 2025.
- Leader: SocGholish (31%), continuing a 2‑year run.
- Top vector: Malvertisement (fake browser updates, poisoned ads/domains).
- New heat: VenomRAT climbed to #4 after its Q1 debut.
- Familiar returns: ClearFake, Mirai, NanoCore back on the board.
- Compounding risk: SocGholish often drops NetSupport, AsyncRAT, and may precede ransomware.
Bluefire takeaway: Prioritize controls that cut malvertising traffic, flag fake‑update chains, and detect RAT post‑exploitation behaviors.
Bluefire Redteam Expert Insights
Field-tested observations from purple team engagements and red team operations in 2024–2025 are listed here. Make use of them to give priority to practical solutions rather than checkbox controls.
1) “Fake Update” Chains Are Faster Than Your Patch Cycle
- We routinely compromise test environments without phishing by chaining malvertising → JS downloader → LOLBins. Browser safe‑browsing features help but don’t cover newly registered domains (NRDs) for hours.
- Bluefire action: Block NRDs and high‑risk ad categories; enforce MSIX/7z execution prompts; detect JS → PowerShell and archive‑spawned processes in EDR.
2) RATs Behave Like Power Users, Not Malware
- Agent Tesla/VenomRAT/NanoCore evade signature‑based tools by “living off the land.” Telemetry showing clipboard access, window enumeration, hidden desktop launches, or screen capture APIs is a stronger signal than family‑specific rules.
- Bluefire action: Implement behavioral detections (e.g.,
powershell.exe+Add-Type+ network beacons), segmentation + egress allow‑lists, and decoy creds to trip hands‑on‑keyboard.
3) IoT Exposure Is a Business Decision
- Mirai‑style exposure persists where facilities, retail, and healthcare rely on default‑credential devices. The fastest wins come from network denial by default and credential sweeps rather than firmware hunts.
- Bluefire action: Quarantine unknown MAC OUIs, run periodic default‑password spray against non‑IT segments, and hard‑block inbound to IoT VLANs.
4) Registrar & Hosting Patterns = Early Warning
- A handful of registrars and edge CDNs recur in the IoC infrastructure. We see strong value in pre‑risking brand‑new assets from high‑velocity registrars/CDNs in secure web gateways.
- Bluefire action: Policy to score NRDs from top recurring registrars/CDNs; temporarily sandbox downloads.
5) Bluefire’s “Ski Slope” Defense Priorities (Tiered)
- Green Runs (fast wins): NRD blocking, ad category filtering, EDR rule pack below, PowerShell transcript logging.
- Blue Runs (mid effort): Browser isolation for internet‑exposed roles, MSIX/7z application control, egress allow‑lists.
- Black Diamond (advanced): Deception beacons, ATT&CK‑mapped purple teaming, Zero Trust segmentation.
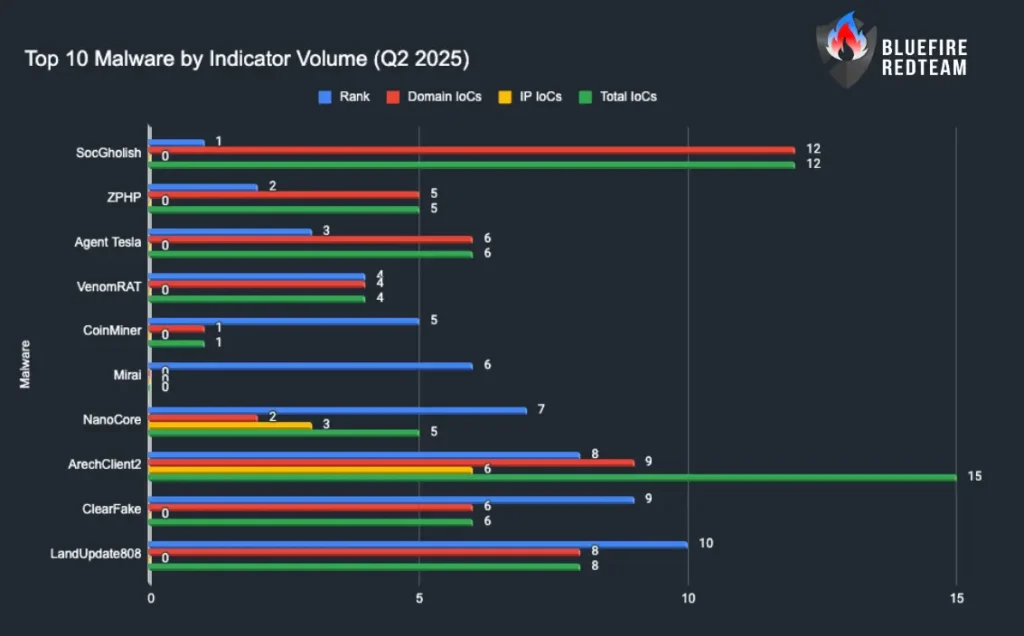
Top 10 Malware (Q2 2025)
- SocGholish — JavaScript downloader through fake browser updates; known for tricks to redirect traffic; often results in data theft and NetSupport/AsyncRAT; in certain instances, it has preceded ransomware.
- ZPHP — JS downloader through fake updates; Lumma Stealer and NetSupport were seen to be dropped.
- Agent Tesla — Commodity RAT for Windows; keylogging, screenshots, cred theft, clipboard capture, file exfil, loader.
- VenomRAT — Variants of the open-source RAT include keylogging, screen capture, cred theft, exfil, and other payloads; recent campaigns exploited typo-squats imitating antivirus brands. It is distributed through malspam or dropped by other malware.
- CoinMiner — The crypto-mining family uses WMI for persistence and lateral movement; it can be dropped or distributed through malspam.
- Mirai — Large DDoS attacks are caused by IoT botnet malware, which is usually released after device vulnerabilities are exploited.
- NanoCore — RAT commonly via malspam (e.g., malicious XLS); broad capabilities incl. persistence via registry.
- ArechClient2 (SectopRAT) — .NET RAT with heavy evasion; profiles systems, steals browser/crypto‑wallet data, launches hidden desktop, anti‑VM/anti‑emulation.
- ClearFake — JS downloader injecting base64 scripts into compromised sites; leverages PowerShell and loads Amadey, Lumma, RedLine, Raccoon v2.
- LandUpdate808 — Fake update chain using MSIX + 7z bundles; installs NetSupport and other tools.
Initial Access: How These Families Get In
Vectors tracked: Dropped • Malspam • Malvertisement • Multiple
- Malvertisement (leader in Q2): SocGholish, ZPHP, ClearFake, LandUpdate808
- Malspam: Agent Tesla
- Dropped: Mirai (post‑exploit)
- Multiple vectors: ArechClient2, CoinMiner, NanoCore, VenomRAT
Control priority:EDR detections for fake update chains, hardened browser policies, and URL filtering and ad-blocking for high-risk categories.
Top 10 Malware by Indicator Volume (Q2 2025)
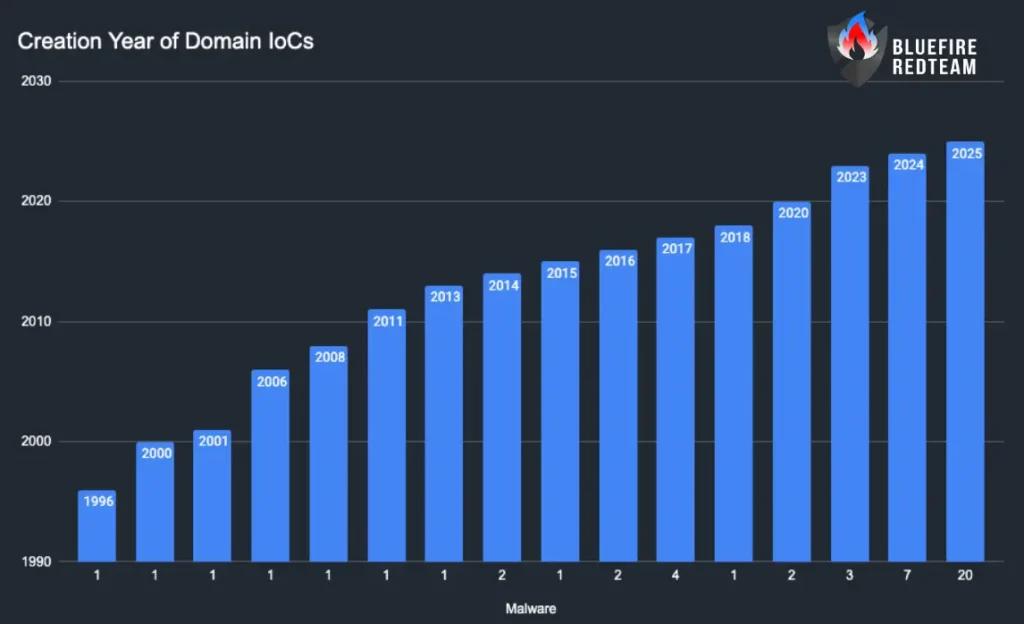
Creation Year of Domain IoCs
Notes: 49/53 domains had current WHOIS; counts below reflect creation years
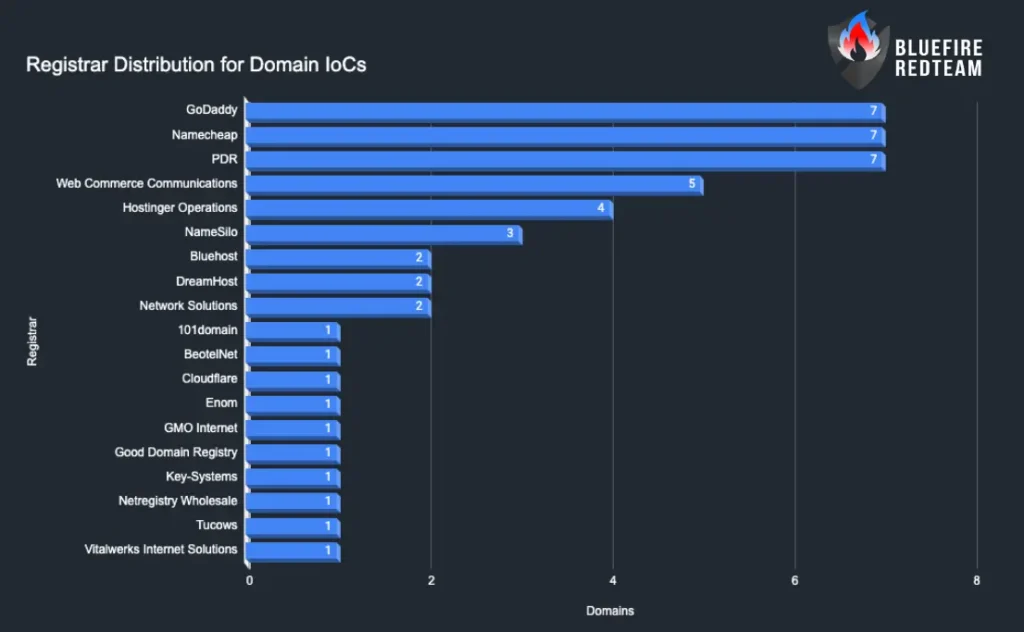
Registrar Distribution for Domain IoCs
Notes: Focus on the top registrars to support early‑warning policies
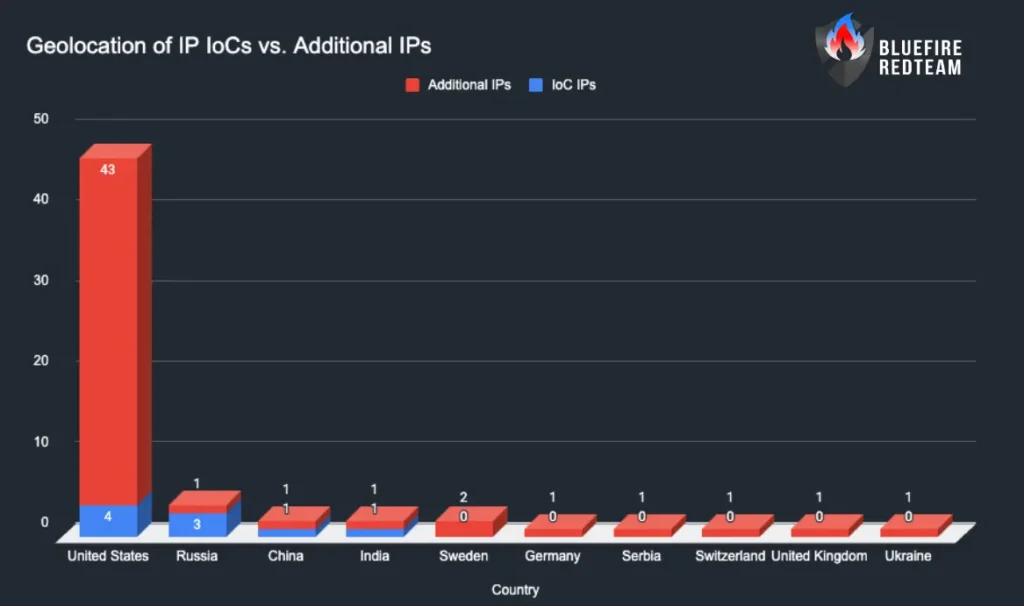
Geolocation of IP IoCs vs. Additional IPs
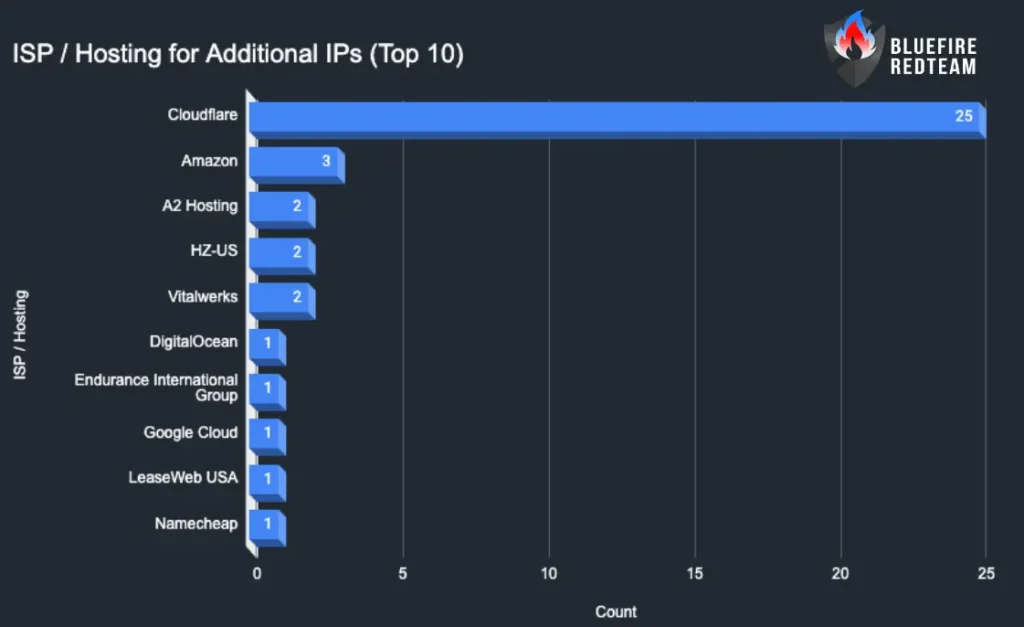
ISP / Hosting for Additional IPs (Top 10)
IoCs: High‑Signal Samples for Threat Hunting
Important: Vet indicators against your environment before blocking. Use these samples for hunt hypotheses and threat intel enrichment.
SocGholish — Domain Samples
ai[.]lanpdt[.]org, app[.]symphoniabags[.]com, billing[.]roofnrack[.]us, cpanel[.]productdevelopmentplan[.]com, folders[.]emeraldpinesolutions[.]com, m[.]cpa2go[.]com, photo[.]suziestuder[.]com, round[.]micha[.]ai, smthwentwrong[.]com, stirngo[.]com, whcms[.]greendreamcannabis[.]com, zone[.]ebuilderssource[.]com
ZPHP — Domain Samples
eddereklam[.]com, islonline[.]org, lqsword[.]top, modandcrackedapk[.]com, textingworld[.]com
Agent Tesla — Domain & Hash Samples
Domains: ftp[.]fosna[.]net, ftp[.]jeepcommerce[.]rs, hosting2[.]ro[.]hostsailor[.]com, myhost001[.]myddns[.]me, sixfiguredigital[.]group, topendpower[.]top
SHA256 (subset): 00179f…c3dcff, 0cd092…c02e2e, 3ac7c6…83093, 550f19…f8ee8, 8406A1…1EABA7, 8e49a4…f06952
VenomRAT — Domain & Hash Samples
Domains: dataops-tracxn[.]com, idram-secure[.]live, bitdefender-download[.]com, royalbanksecure[.]online
SHA256 (subset): 075f99…5f2ea, 820a44…f794f, Aa0587…82ee4, Adbce5…54cb7, B2AE69…A33F3
CoinMiner — Domain & Hash Samples
Domain: xmrminingproxy[.]com
SHA256 (subset): 47ecaab…76f8ca, 6FB494…A17443, 72F1BA…084BE, 8A4929…5C30D
Mirai — Hash Samples
11C044…A4114, 438DC2…460B5, 7461C0…F036A1, F05247…F6714
NanoCore — Domains, IPs & Hash Samples
Domains: louinc928[.]gotdns[.]ch, x02e2069bb8744[.]anondns[.]net
IPs: 123[.]123[.]123[.]123, 193[.]161[.]193[.]99, 74[.]77[.]124[.]104
SHA256 (subset): 069ced…8c043, 09bbc4…d2abf, 4d190f…2f6716, 62c5fb…49d6f9
ArechClient2 — Domains, IPs & Hash Samples
Domains: bienvenido[.]com, bind-new-connect[.]click, candyconverterpdf[.]com, candyxpdf[.]com, chrome[.]browser[.]com[.]de, key-systems[.]net, launchapps[.]site, promooformosa[.]com, server786[.]ninositsolution[.]com
IPs: 143[.]110[.]230[.]167, 144[.]172[.]97[.]2, 172[.]86[.]115[.]43, 45[.]129[.]86[.]82, 45[.]141[.]87[.]16, 45[.]141[.]87[.]218
SHA256 (subset): 1da2b2…e1570, 515EA9…D578, 7F386E…AE81
ClearFake — Domain Samples
bandarsport[.]net, bip32[.]katuj[.]fun, getlastingro[.]com, kargotrong[.]com, ratatui[.]today, yuun[.]pages[.]dev
LandUpdate808 — Domain Samples
alhasba[.]com, edveha[.]com, jimriehls[.]com, nypipeline[.]com, rajjas[.]com, skatkat[.]com, swedrent[.]com, waxworkx[.]com
Defensive Playbook (Mapped to CIS Controls® & MITRE ATT&CK®)
Malvertising / Fake‑Update Chains
- CIS Controls: 1, 2, 7, 9, 13, 14
- Quick wins:
- Enforce browser isolation or enhanced safe browsing modes for high‑risk sites.
- Block ad categories and newly registered domains (NRDs) at the edge.
- Roll out application control to restrict installers (MSIX/7z) and unsigned binaries.
- EDR detections for JavaScript‑spawned PowerShell, LOLBins, and archive‑spawned processes.
- Bluefire detections to deploy:
- Sigma/EDR:
wscript.exeormshta.exe→powershell.exewith-EncodedCommand. - Sigma/EDR: Parent=
browser→ child=powershell/rundll32within 3 minutes of download. - Network: NRD egress to ad/track domains over DoH/DoT.
- Policy‑as‑code (FW/Proxy): Block
.msixand.7zfrom new/uncategorized domains; sandbox first occurrence.
- Sigma/EDR:
RAT Post‑Exploitation (Agent Tesla, VenomRAT, NanoCore, ArechClient2)
- CIS Controls: 3, 4, 5, 6, 8, 10, 16
- Quick wins:
- Credential hardening: turn off legacy auth, enforce PAM/SSO, secret rotation.
- Network segmentation; egress filtering for RAT C2 patterns.
- Endpoint telemetry: clipboard access, screenshot capture, and persistence keys.
- Deception beacons on high‑value hosts to detect interactive control.
- Bluefire detections to deploy:
- Hunt: hidden desktop creation (ArechClient2) and WinAPI screen capture imports.
- Hunt: Abnormal clipboard access loops + process hollowing indicators.
- Policy‑as‑code (EDR): Block credential‑stealer families by behavior (browser secrets access + outbound POST bursts).
IoT & Edge (Mirai)
- CIS Controls: 1, 4, 11, 12
- Quick wins:
- Inventory & quarantine unknown devices; default credential sweeps.
- Auto‑patch exposed services; deny‑all inbound to IoT networks.
- Rate‑limit and scrub outbound UDP amplification patterns.
- Bluefire detections to deploy:
- NIDS: signatures for telnet/ssh brute + default creds; flow anomalies from IoT VLANs.
- NAC: MAC OUI allow‑lists with auto‑quarantine.
Bluefire Redteam: What We’ll Do for You
- Attack Surface Audit (free, 30 minutes): Find NRDs, malvertising‑exposed paths, and fake‑update weak points.
- Malvertising Threat Simulation: Recreate SocGholish/ClearFake chains against a sandboxed mirror of your org to expose control bypasses.
- RAT Containment Readiness Assessment: Validate detections for Agent Tesla / VenomRAT / NanoCore techniques (exfil, persistence, screen capture, hidden desktop).
- IoT Edge Hardening Sprint: Rapid posture uplift for Mirai‑style risks across cameras, appliances, and branch gear.
- Quarterly Threat Review (QBR): Brief execs on infra trends (registrars/CDNs, NRDs, IP geo shifts) and tune policies.
- Bluefire Rule Pack: Sigma/EDR queries + proxy policies updated quarterly.
Methodology & Attribution
- The MS-ISAC/CIS Top 10 primary dataset was obtained from public CTI reporting for the second quarter of 2025. To create registrant, registrar, hosting, and geo views, we normalised IoC sets (domains, IPs, and hashes) and enhanced them with WHOIS/DNS metadata. For count-based charts, we eliminated duplicates and non-resolving artefacts. Before being enforced, indicators for defensive research must be validated in the environment.
- Bluefire added detection guidance based on internal adversary emulation and purple team exercises.
Attribution
This brief synthesizes Q2 2025 malware insights and IoCs originally published by reputable threat intelligence sources. All indicators are provided strictly for defensive research and require validation prior to enforcement.
Contact us for next-gen cybersecurity capabilities


