The risks associated with cloud adoption are also rapidly increasing. Cloud breaches across industries are on the rise in 2025 due to misconfigurations, noncompliance, and budgetary constraints.
This article dives into the key statistics, highlights where organizations are falling short, and explores how to allocate the right budgets to stay secure.
The Misconfiguration Crisis
Misconfigurations continue to be one of the top causes of cloud breaches:
- 15% of breaches begin with cloud misconfigurations—the 3rd most common attack vector in 2024
- Gartner predicts that by 2025, 99% of cloud failures will be due to customer error
Nearly 23% of cloud security incidents stem directly from misconfigurations, with 27% of businesses reporting public cloud breaches
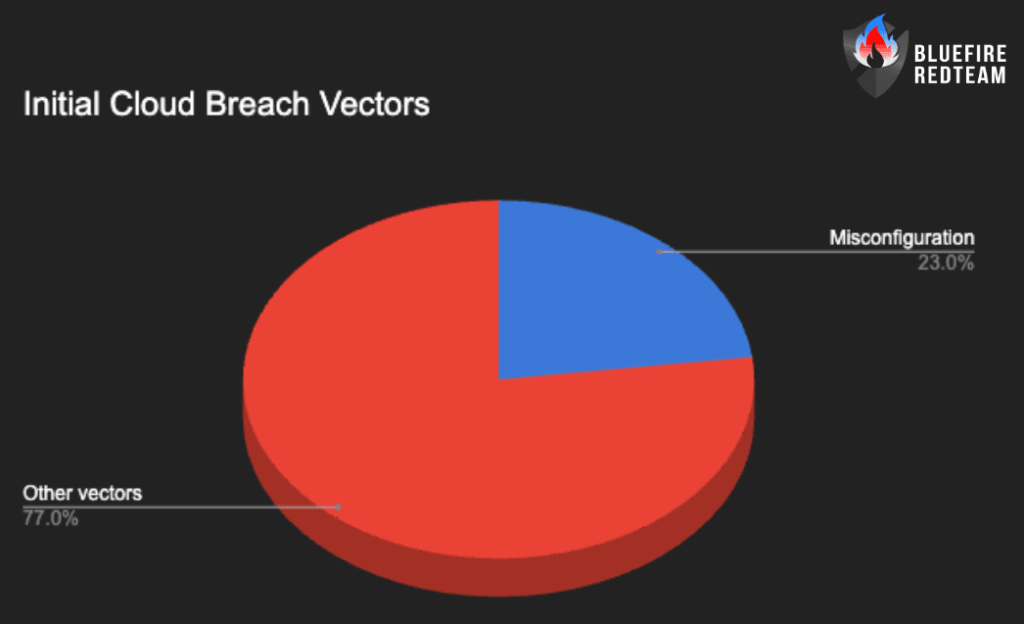
Rising Cloud Breach Incidents
Cloud-focused breaches are becoming the norm:
- 82% of data breaches in 2023 involved cloud-stored data
- Cloud environment intrusions rose 75% between 2022 and 2023, according to CrowdStrike
Exposed Secrets & Data
Misconfigurations aren’t just theoretical—they’re exposing real data:
- 54% of cloud environments have exposed VMs/serverless instances with sensitive data
- 9% of public cloud storage contains sensitive PII/payment data
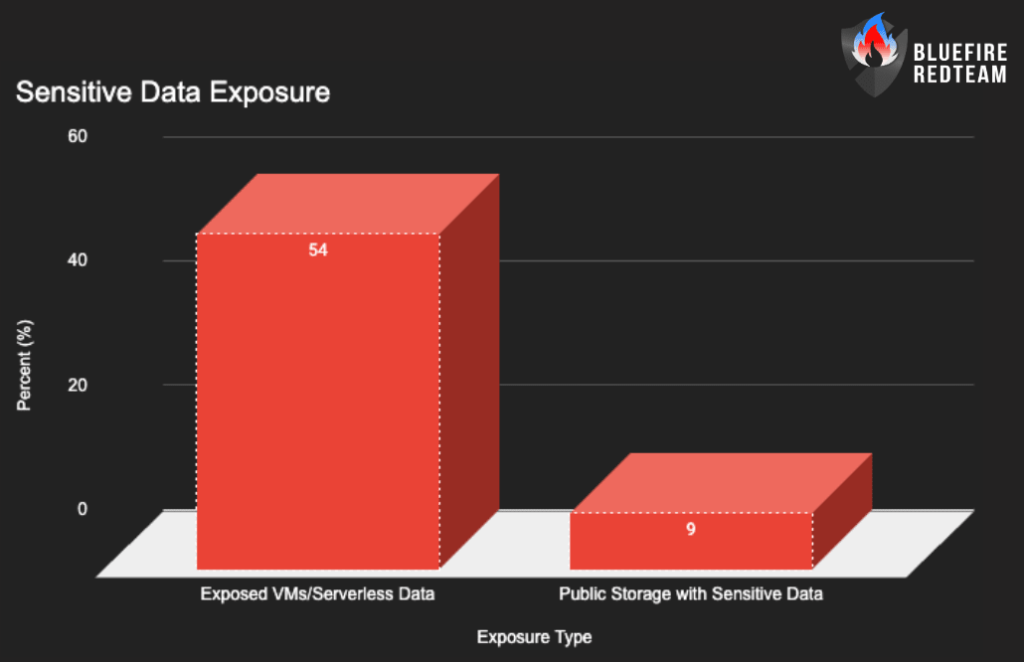
Cloud Budget Gaps
Security readiness often falls short—even as threats rise:
- 15% of UK businesses still lack any cybersecurity budget
- 23% have no plans to increase spending
- 58% of smaller businesses lack dedicated security budgets
The Human Factor
Human error remains the weakest link:
- 80% of organizations have experienced a cloud security incident in the past year
- 45% struggled with cloud misconfigurations due to training and awareness gaps
Why These Stats Matter
These figures highlight:
- Misconfigurations that result in significant vulnerabilities
- Inconsistency between security investment and new threats
- Over half of environments exposing sensitive data
- Attacks are made easier by inadequate training.
Together, they show that most organizations aren’t prepared for cloud-scale risks.
Expert Insights from Bluefire Redteam
“The most common attack vector is still misconfiguration, which can be completely avoided with automation and continuous monitoring.” — Bluefire Redteam
What You Should Do Now
- Automate misconfiguration detection: Use Cloud Infrastructure Security or CSPM tools to automatically detect misconfigurations.
- Allocate dedicated security budgets: Set aside funds specifically for security based on incident risk profiles.
- Provide continuous training: Target misconfigurations in storage, API, and IAM
- Benchmark monthly: How many environments report secrets exposure?
- Engage experts: Regular audits + red team exercises uncover hidden risks
👉 Explore our Cloud Risk Assessment & Pentesting Services
Conclusion
Human error and misconfigurations are the main causes of the growing number of cloud breaches. It’s time to take prevention and financial management seriously, as more than half of environments expose sensitive data.
If you’re worried your cloud defenses aren’t keeping up, Bluefire Redteam can help you baseline, harden, and secure your cloud with expert services.


